For Cloud field day 21 we listened to some of the new solutions from VMware by Broadcom for 3 hours of sessions. I had originally intended to write individual posts, but the high amount of information that came hot and heavy from VMware and my fellow delegates made it very interesting to keep up, so instead I’ll place all this information in a centralized location
I have 2 other blogs covering the high level of both VMware, and VCF. For these I’m going to try to cover the deeper engineering slides of VCF and the different solutions built within it.
VCF Consolidation and Migration
When you are building VCF you will eventually be faced with the challenge of combining VCF environments together. Lots of customers have ran into this problem and now VMware has an answer. By utilizing SDDC Manager now there is a script to import a cluster into SDDC manager so it can then be managed by a single SDDC Manager.

HCX has been around for the VMC on AWS solution sets, but now it’s available for VCF customers. HCX is only a migration tool, it is not a tool for replacing DRS or working in the same way. HCX works by creating an interconnect from one site to the other, then setting up the network landing zones between and also setting up the individual needs to ensure availability across both locations. A cool callout was that most hyperscalers have an HCX service already setup to help support customers looking to migrate their workloads onto their platform. I’ve used HCX several times, and to be honest figuring out the networking pieces is a challenge and difficult to get working, but once its working its a solid solution that very rarely has failed me to migrate workloads to and from an endpoint.
VCF Monitoring
Monitoring a VCF deployment is a key part of the VI Admins day to day life. After waking up from, hopefully, no pager duty alerts, they come into the office and normally the first thing they look at is the health of their environment. This is all don’t through Aria Operations within the VCF licensing.
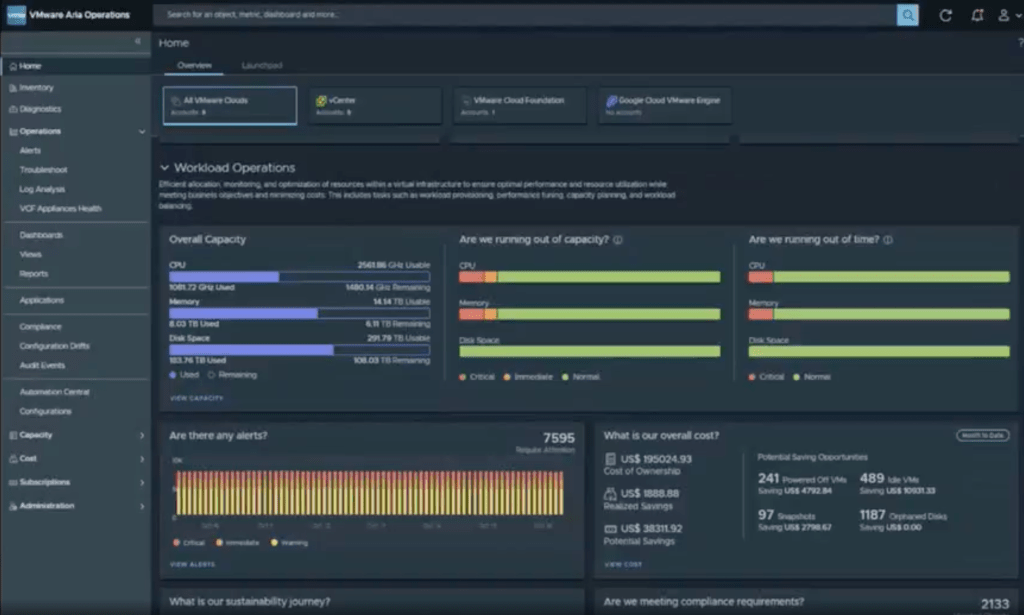
The dashboard provided via Aria Operations shows a quick snapshot on the alerts that need to be investigated, and also things like cost, and capacity. From there you can look into the workbench and dashboards to investigate the requirements of solutions.
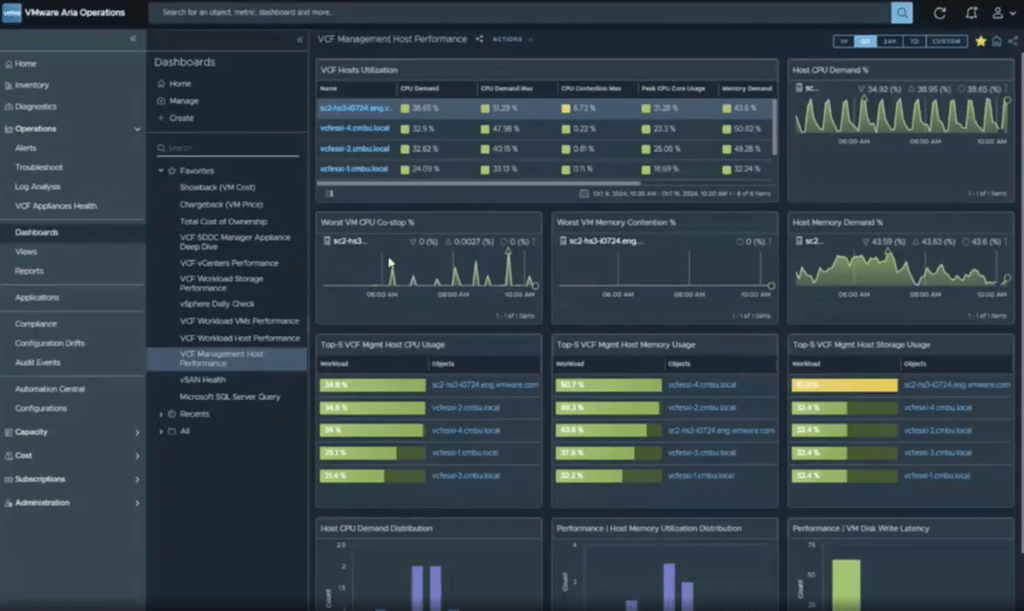
As a user of Aria Operations before, I really appreciated the ability to dive into alerts and see what is the issue that caused the alert, because investigating the alert is a difficult thing for VI Admins especially when additional alerts are added that are outside of their domain. For instance seeing CPU/Memory alerts is always an application issue on a virtual machine, but figuring out which caused it and how it needs to be addressed isn’t always an question that the VI admin can answer so they will need to work on with additional groups. One aspect I enjoy hearing from the monitoring side of things is just how much granularity you have to manage the environments. You can adjust where the moderate risk, or critical risk or more level is, so that it’s honed to the organization, that Operations is built in. On top of monitoring and management, the ability is there for upsizing virtual machines and downsizing them, as well as scheduling jobs in order to support these regular tasks so that VI Admins can have a break from the mundane tasks they have to do daily.
VMware, and Kubernetes

The direct first statement VMware made is that what we are seeing, and what is above as an illustration is not Tanzu, this is VCF and what is available out of the box with VCF. VMware Kubernetes Service is the new name for an old friend, as this is what is used to build Kubernetes clusters on-premises as well as having additional integrations within the clusters to allow external connections and solutions to be added to the environment.
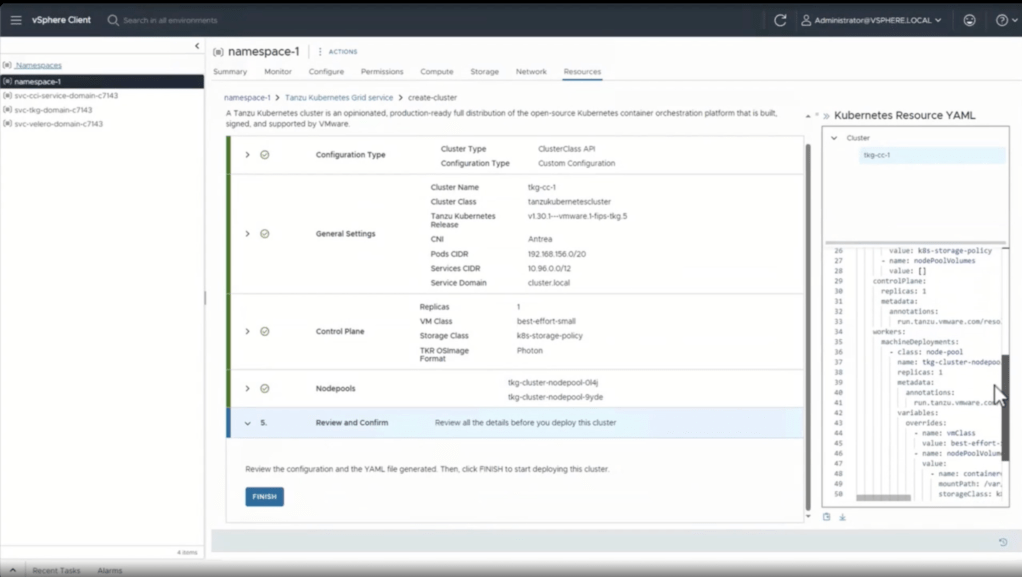
From my perspective there is a lot that has been repurposed from TKG in this space but the critical piece illustrated above is that there is now a yaml output for deploying the cluster. Allowing users to be able to understand what is deployed and utilize a way to deploy the same cluster in a quick and repeatable way is powerful to change how an organization works for their day to day. There was some discussion about who would be able to fill out the request to build the cluster, and really, the answer is to work with developers to understand what they are looking to provide, and help build the cluster required to meet those needs based on the releases available, and the node requirements. At the end Kat shows the ability to update the supervisor cluster to deploy newer versions of Kubernetes and it really helped forecast how simple it is now to update your releases and get them available for customers.
VMware Automation
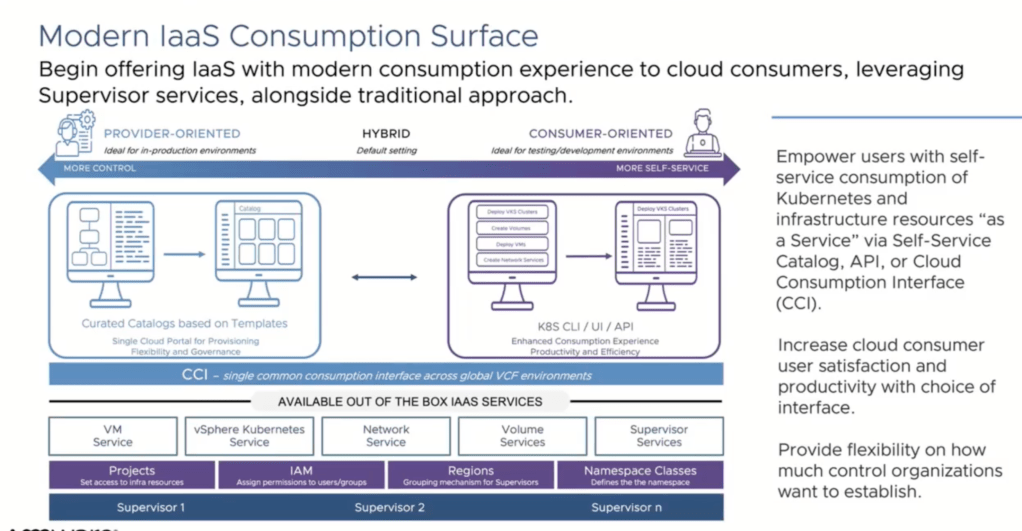
The automation area is definitely a passion of mine. I’ve worked within vRealize Automation, and Aria for the past 10 years, and have enjoyed the additional changes that are created. Based on the new solutions with VMware Automation they are integrating a lot of the VKS solutions that were shown previously within the Kubernetes space and expand on it based on what Automation can now do. For those that have not worked in the space, there was a real challenge between Aria Automation, and Tanzu, because they both worked around the same space and it ended up being a choice based on the customers culture and what they are comfortable with using. Now there is a direct integration between Kubernetes and automation to bring self-service to a catalog in order to build the cluster by users, instead of only through the administrator.
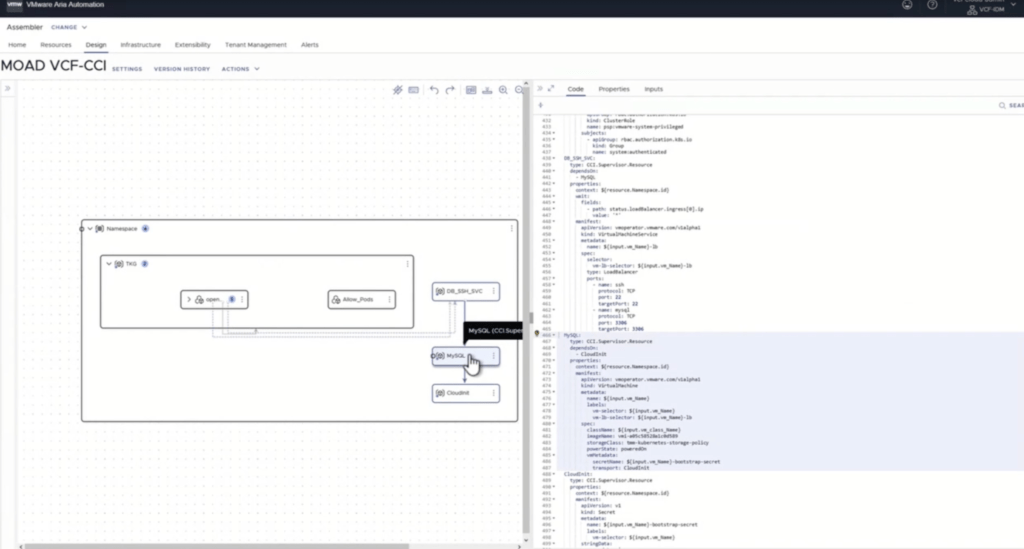
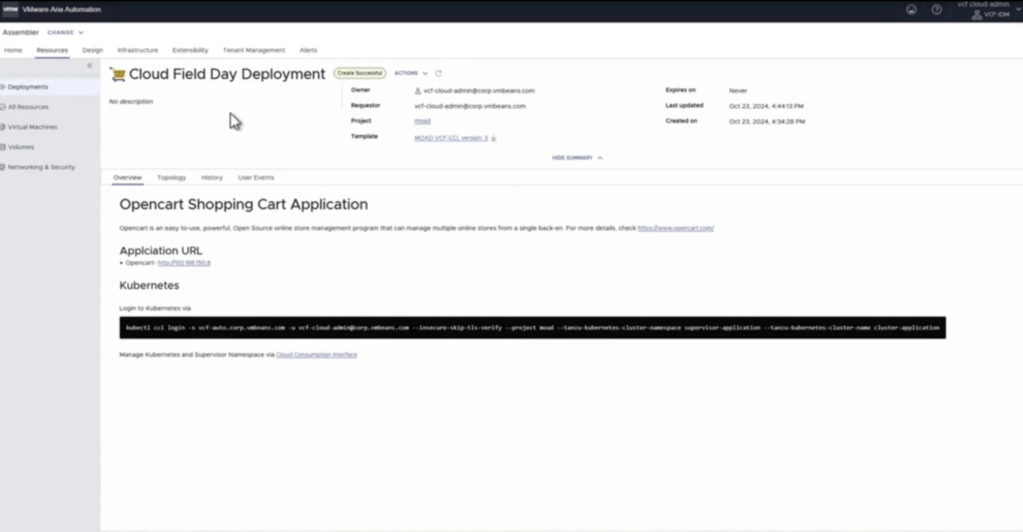
In the above the deployment we saw in the vide we were able to see aria deploy a Kubernetes cluster within a supervisor namespace and then deploy services within Kubernetes. This capabilities have been discussed but this is the first time that I have seen it working. On top of seeing the solution actually build a cluster and the solutions when going into the resource to look at what was built you can then see the command to log into kubernetes.
VCF Security

It’s a joy to hear Bob Plankers just because I don’t think he knows how to speak down to people, and up is the only way it works with him. Speaking toward the goal of VCF security at a high level is a good direction for VCF. I work with government groups that need to ensure insane security and compliance so it’s worth the time to discuss what VCF is able to achieve in its deployment. Even security can be a challenge for air gapped environment, so the idea of having that the solution would be secure right out of the box is a wonderful start from start to finish.

Security out of the box, starts with the box. This is why VMware has been working with a number of providers including CPU manufacturers and other groups in order to enable security and following that there are additional security, like VIBs and what is ran and software ran virtually for the virtualization built upon the box.
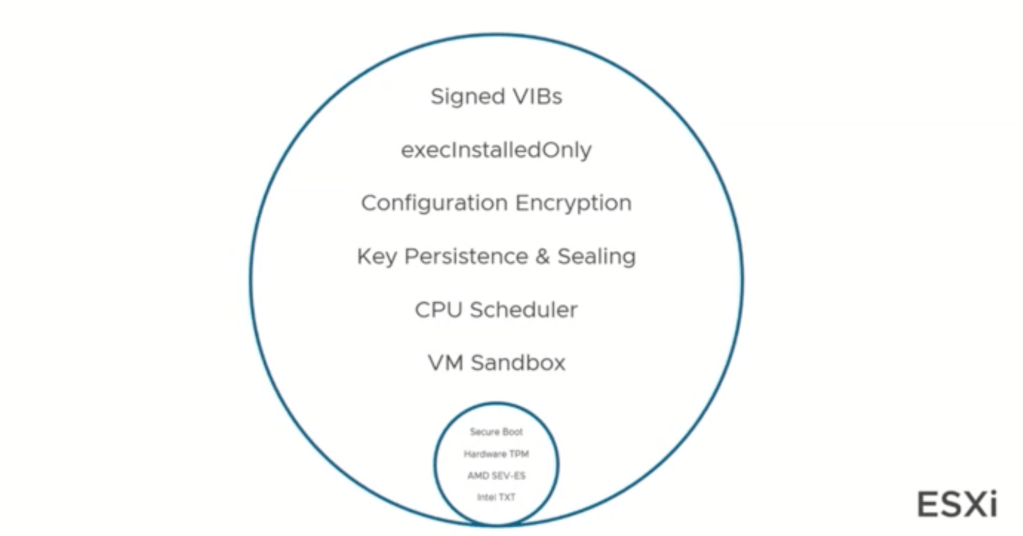
Next iteration after the deployment of the hypervisor on the hardware is the hypervisor itself. This also includes encryption, key persistence and more as illustrated above. This is critical to organizations to ensure that they are able to utilize the security solutions upon the hypervisor itself.

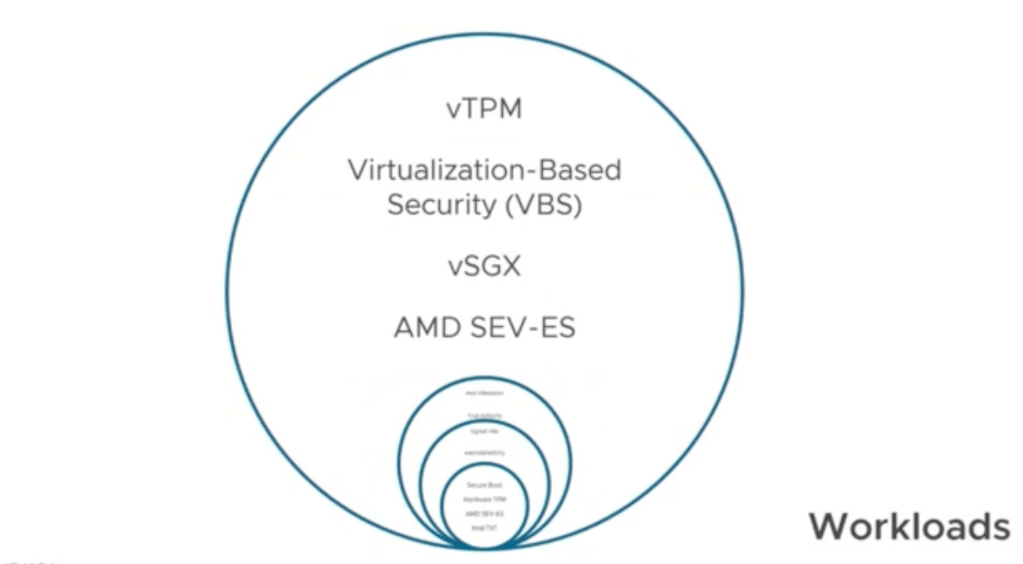
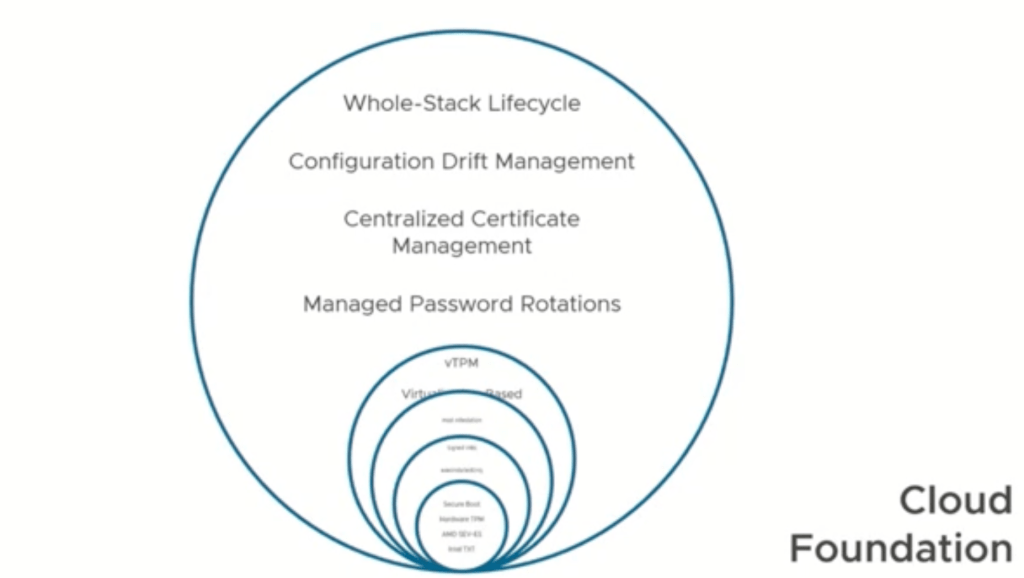
Taking a wholistic view of security out of the box is a great direction for the leading hypervisor on the market. Bob also discussed using declarative code in order to state how hosts should be build, as well as allowing fast patch to patch hosts without disrupting the hosts and causing downtime within the environment. This is something that has been shown with different operating systems as well, but what it entails is utilizing virtualization to patch services and then migrate back what is updated to ensure uptime. Lifecycle manage is also enhanced to add, and remove components based on the hardware manufacturer now making it easier to add firmware and hardware requirements that need to be updated in order to run properly. vCenter updates now follow the same methodology by building a new vCenter and then migrating the data to the new vCenter after updating so it then solves the problem of downtime for a vcenter allowing only blips of downtime rather than possible large downtimes. The goal behind this is to ensure that customers actually patch and use the security solutions within VMware instead of holding off because of the organizations or culture.
Conclusion:
If it wasn’t for VMware, I wouldn’t be in tech at the level that I am. I grew as a VI Admin, and automation specialist and that started from learning how to migrate, or reboot VMs, into building them, into managing and solving problems within the VMware environment. VMware Cloud Foundations is a solid solution for enterprise customers, and this iteration is showing the next level of capability for customers. The newer things that were shown like Kubernetes being integrated with Aria now is fantastic, as well as the ability to migrate clusters together within VCF. These are great additions to a solid offering from VMware. Looking at the Kubernetes solution, the addition of VKS to the stack and removing it from the integration for vCenter is a solid choice as this has added crashes to vCenter and added additional support requests for customers to remove what is needed to be removed.
As a whole from start to finish, VMware came and stood their ground to a hostile group. We all knew the challenges customers are running into with VMware and licenses, however the group we saw understood the missteps of the past year and want to fix them in the next. I think there is hope here for folks that are anxious of their VMware environment and licensing, but only time will tell.
